The Certified Ethical Hacker course is the most desired information security training program any information security professional will ever want to be in. To master the hacking technologies, you will need to become one, but an ethical one! The accredited hacking course provides the advanced hacking tools and techniques used by hackers and information security professionals alike to break into an organization. As we put it, “To beat a hacker, you need to think like a hacker”.
This Hacking course will immerse you into the Hacker Mindset so that you will be able to defend against future attacks. The security mindset in any organization must not be limited to the silos of a certain vendor, technologies or pieces of equipment. This ethical hacking course puts you in the driver’s seat of a hands-on environment with a systematic process. Here, you will be exposed to an entirely different way of achieving optimal information security posture in their organization; by hacking it! You will scan, test, hack and secure your own systems. You will be taught the five phases of ethical hacking and the ways to approach your target and succeed at breaking in every time! The five phases include Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering your tracks.

Ethical Hacking , Information Security , Cyber Security Trainings & Certification
EC-Council Certification Courses Road-Map 2025-2026 (Download it)
https://www.eccouncil.org/wp-content/uploads/2023/02/Cyber-Handbook-Enterprise.pdf
The weakest link in an organization's IT security plan is often its own employees. Using social engineering, malicious emails, phishing, and other tactics, criminals are often able to trick employees into disclosing private information or bringing malware inside an organization. In recent surveys, nearly half of all security, risk, and compliance officers have indicated that their own employees are a greater risk than hackers or hacktivists. Cyber awareness training can help your organization address this. We Provide Security from Facebook Hacking, Twitter Hacking, Whatsapp Hacking, Instagram Hacking, Linkedin Hacking, Website Hacking, Email account Hacking, Gmail Hacking , Yahoo account Hacking, Social Media account Hacking. Our responsibilities to work on Schools, Colleges, Universities, Education Sector, Govt. Organization, Banks, Private Sector & Misc. Organization on Cyber Security Awareness, Ethical Hacking CEH Awareness, Cyber Drills in Pakistan and COP Child Protection Law Projects. As PISA Pakistan Information Security Coordinator Punjab, We Invited all Security Agencies, Organization, Companies, Colleges & Universities Students, Professors, Deans Organized Workshop / Seminars on Cyber Security, Ethical Hacker & Child Online Protection. We offer CEH Online Training in Lahore Pakistan. Ethical Hacking Training in Pakistan

Certified Ethical Hacking CEH Course
in Lahore Pakistan
Download CEH Ethical Hacker Brochure
Advance Ethical Hacking Course in Lahore
Course Outline:
Module
01: Introduction to Ethical Hacking
Module 02: Footprinting and
Reconnaissance
Module 03: Scanning Networks
Module 04: Enumeration
Module 05: Vulnerability Analysis
Module 06: System Hacking
Module 07: Malware Threats
Module 08: Sniffing
Module 09: Social Engineering
Module 10: Denial-of-Service
Module 11: Session Hijacking
Module 12: Evading IDS, Firewalls, and
Honeypots
Module 13: Hacking Web Servers
Module 14: Hacking Web Applications
Module 15: SQL Injection
Module 16: Hacking Wireless Networks
Module 17: Hacking Mobile Platforms
Module 18: IoT Hacking
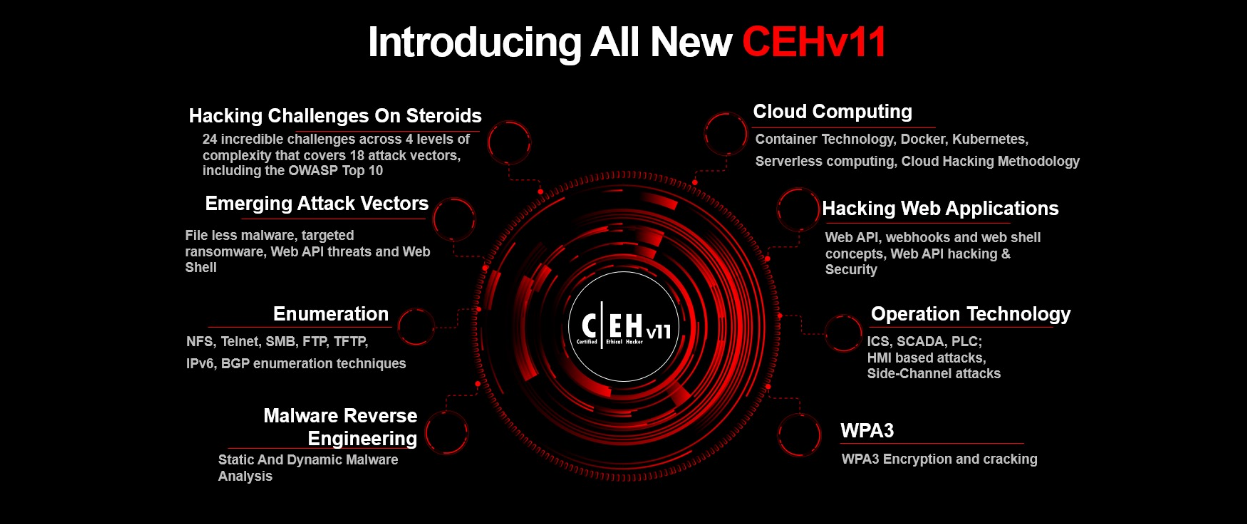
Module 19: Cloud Computing
Module 20: Cryptography
Ethical Hacking CEH training course in Lahore Pakistan, CEH Ethical Hacking training Institute in Lahore Pakistan , puts you in the driver's seat of a hands-on environment with a systematic process. Here, you will be exposed to an entirely different way of achieving optimal information security posture in their organization; by hacking it! You will scan, test, hack and secure your own systems. You will be taught the five phases of ethical hacking and thought how you can approach your target and succeed at breaking in every time! The five phases include Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering your tracks. Underground Hacking Tools , The hacking tools and techniques in each of these five phases are provided in detail in an encyclopedic approach to help you identify when an attack has been used against your own targets. Why then is this training called the Certified Ethical Hacker Course? This is because by using the same techniques as the bad guys, you can assess the security posture of an organization with the same approach these malicious hackers use, identify weaknesses and fix the problems before they are identified by the enemy, causing what could potentially be a catastrophic damage to your respective organization. Hacking Training in Lahore Pakistan. Ethical Hacking CEH Training in Lahore Pakistan

CEH Advance Ethical Hacking training Institute in Lahore Pakistan. We live in an age where attacks are all susceptible and come from anyplace at any time and we never know how skilled, well-funded, or persistent the threat will be. Throughout the CEH course, you will be immersed in a hacker's mindset, evaluating not just logical, but physical security. Exploring every possible point of entry to find the weakest link in an organization. From the end user, the secretary, the CEO, misconfigurations, vulnerable times during migrations even information left in the dumpster. Hackers are innovators and constantly find new ways to attack information systems and exploit system vulnerabilities. Savvy businesses proactively protect their information systems by engaging the services and expertise of IT professionals skilled in beating hackers at their own game (often called "white hat hackers" or simply "white hats"). Hacking Training in Lahore Pakistan
Cyber Security training Institute in Lahore Pakistan, Such professionals use the same skills and techniques hackers use to identify system vulnerabilities and access points for penetration, and to prevent unwanted access to network and information systems. Information Security Training in Pakistan, We offer Certified Ethical Hacker (CEH) is an intermediate-level credential offered by the International Council of E-Commerce Consultants (EC-Council). It's a must-have for IT professionals pursuing careers in ethical hacking. Cyber Security training course in Lahore Pakistan , CEH credential holders possess skills and knowledge on hacking practices in areas such as foot printing and reconnaissance, scanning networks, enumeration, system hacking, Trojans, worms and viruses, sniffers, denial-of-service attacks, social engineering, session hijacking, hacking web servers, wireless networks and web applications, SQL injection, cryptography, penetration testing, evading IDS, firewalls, and honey pots. Kali Linux Backtrack Operating System training in Lahore Pakistan. Ethical Hacking Training in Lahore Pakistan


Course Description
Student Shelter In Computers CEH Ethical
Hacking Training Institute in Lahore Pakistan. This class will immerse the students into an interactive environment where they
will be shown how to scan, test, hack and secure their own systems. The lab
intensive environment gives each student in-depth knowledge and practical
experience with the current essential security systems. Students will begin by
understanding how perimeter defenses work and then be lead into scanning and
attacking their own networks, no real network is harmed. Students then learn how
intruders escalate privileges and what steps can be taken to secure a system.
Students will also learn about Intrusion Detection, Policy Creation, Social
Engineering, DDoS Attacks, Buffer Overflows and Virus Creation. When a student
leaves this intensive 5 day class they will have hands on understanding and
experience in Ethical Hacking. This course prepares you for EC-Council Certified
Ethical Hacker exam 312-50 , Cyber Security Training Course in Lahore
Pakistan Download Ethical Hacker CEH Brochure

About CEH Course
The Certified Ethical Hacker C|EH program is a trusted and respected ethical hacking training Program that any
information security professional will need. Since its inception in 2003, the
Certified Ethical Hacker has been the absolute choice of the industry globally.
It is a respected certification in the industry and is listed as a baseline
certification on the United States Department of Defense Directive 8570. The C|EH exam is ANSI 17024 compliant adding credibility and value to credential
members.
C|EH is used as a hiring standard and is
a core sought after certification by many of the Fortune 500 organizations,
governments, cybersecurity practices, and a cyber staple in education across
many of the most prominent degree programs in top Universities around the globe.
Hundreds of Thousands of InfoSec Professionals as well as Career Starters have
challenged the exam and for those who passed, nearly all are gainfully employed
with successful careers, but the landscape is changing. Cyber Security as a
profession is evolving, the barrier to entry is
rising, the demand for Skilled Cyber professionals continues to grow, but it is
being refined, demanding a higher level of skill and ability. EC-Council raises
the bar again for ethical hacking training and certification programs with the
all new C|EH
This
course will immerse you into a “Hacker Mindset” in order to teach you how to
think like a hacker and better defend against future attacks. It puts you in the
driver’s seat with a hands-on training environment employing a systematic
ethical hacking process. You are constantly exposed to creative techniques of
achieving optimal information security posture in the target organization; by
hacking it! You will learn how to scan, test, hack and secure target systems.
The course covers the Five Phases of Ethical Hacking, diving into
Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering
your tracks. The tools and techniques in each of these five phases are provided
in detail in an encyclopedic approach and absolutely no other program offers you
the breadth of learning resources, labs, tools and techniques than the C|EH
program.

Certification
The Certified Ethical Hacker exam 312-50 may be taken on the last day of the
training (optional). Students need to pass the online Pearson
VUE exam to receive
CEH certification.
Legal Agreement
Ethical Hacking and Countermeasures course mission is to educate, introduce and
demonstrate hacking tools for penetration testing purposes only. Prior to
attending this course, you will be asked to sign an agreement stating that you
will not use the newly acquired skills for illegal or malicious attacks and you
will not use such tools in an attempt to compromise any computer system, and to
indemnify EC-Council with respect to the use or misuse of these tools,
regardless of intent.
Not anyone can be a student — the Accredited
Training Centers (ATC) will make sure the applicants work for legitimate
companies.
About the Certified Ethical Hacker
(Practical)
C|EH Practical is a six-hour, rigorous exam
that requires you to demonstrate the application of ethical hacking techniques
such as threat vector identification, network scanning, OS detection,
vulnerability analysis, system hacking, web app hacking, etc. to solve a
security audit challenge.
This is the next step after you have attained the highly acclaimed
Certified Ethical Hacker certification.
Professionals that possess the C|EH credential will be able to sit
for exam that will test them to their limits in unearthing vulnerabilities
across major operating systems, databases, and networks.
You will be given limited time, just like in the real world. The
exam was developed by a panel of experienced SMEs and includes 20 real-life
scenarios with questions designed to validate essential skills required in the
ethical hacking domains as outlined in the C|EH program.
It is not a simulated exam but rather, it mimics a real corporate
network through the use of live virtual machines, networks, and applications,
designed to test your skills. You will be presented with scenarios and will be
asked to demonstrate the application of the knowledge acquired in the C|EH
course to find solutions to real-life challenges.

CEH (Practical) Credential Holders Are Proven To Be Able To:
Demonstrate the understanding of attack
vectors
Perform network scanning to identify live
and vulnerable machines in a network.
Perform OS banner grabbing, service, and
user enumeration.
Perform system hacking, steganography,
steganalysis attacks, and cover tracks.
Identify and use viruses, computer worms,
and malware to exploit systems.
Perform packet sniffing.
Conduct a variety of web server and web
application attacks including directory traversal, parameter tampering, XSS,
etc.
Perform SQL injection attacks.
Perform different types of cryptography
attacks.
Perform vulnerability analysis to
identify security loopholes in the target organization’s network, communication
infrastructure, and end systems etc.
.png)
What will you learn?
1. Key issues plaguing the information security world, incident management
process, and penetration testing.
2. Various types of footprinting, footprinting tools, and countermeasures.
3. Network scanning techniques and scanning countermeasures.
4. Enumeration techniques and enumeration countermeasures.
5. System hacking methodology, steganography, steganalysis attacks, and covering
tracks.
6. Different types of Trojans, Trojan analysis, and Trojan countermeasures.
7. Working of viruses, virus analysis, computer worms, malware analysis
procedure, and countermeasures.
8. Packet sniffing techniques and how to defend against sniffing.
9. Social Engineering techniques, identify theft, and social engineering
countermeasures.
10. DoS/DDoS attack techniques, botnets, DDoS attack tools, and DoS/DDoS
countermeasures.
11. Session hijacking techniques and countermeasures.
12. Different types of webserver attacks, attack methodology, and
countermeasures.
13. Different types of web application attacks, web application hacking
methodology, and countermeasures.
14. SQL injection attacks and injection detection tools.
15. Wireless Encryption, wireless hacking methodology, wireless hacking tools,
and Wi-Fi security tools.
16. Mobile platform attack vector, android vulnerabilities, mobile security
guidelines, and tools.
17. Firewall, IDS and honeypot evasion techniques, evasion tools, and
countermeasures.
18. Various cloud computing concepts, threats, attacks, and security techniques
and tools.
19. Different types of cryptography ciphers, Public Key Infrastructure (PKI),
cryptography attacks, and cryptanalysis tools.
20. Various types of penetration testing, security audit, vulnerability
assessment, and penetration testing roadmap.
21. Perform vulnerability analysis to identify security loopholes in the target
organization’s network, communication infrastructure, and end systems.
22. Different threats to IoT platforms and learn how to defend IoT devices
securely

What is the Role of AI in Cybersecurity?
Artificial Intelligence Course in Lahore Pakistan By Student Shelter In Computers. Before AI, conventional systems were less efficient in detecting and tackling unknown attacks, resulting in misleading outputs that proved hazardous to an organization’s security framework. However, the traditional approach saw a significant advancement with AI in addressing these challenges and delivering result-driven outcomes. Nowadays, AI cybersecurity solutions are seen as a driving force, owing to their capability to navigate threats in advance and suggest solutions to gain the upper hand over cybercriminals.
Artificial Intelligence and Cyber Security Course in Lahore. The rise of AI in the face of escalating threats has been instrumental in dealing with ever-evolving security challenges and developing strategies ahead of time. Organizations are now leveraging artificial intelligence and security along with professional expertise and new tools to protect their sensitive data and critical systems. AI-based solutions can help keep pace with emerging threats, detect and respond to new threats, and offer better cyber protection. However, like two sides of a coin, AI can be both a blessing and a curse. As a result, AI cybersecurity has become essential in safeguarding modern digital infrastructures. Artificial intelligence in security provides numerous benefits, particularly in how threats are detected and remediated. AI algorithms work on a proactive approach to analyzing data and identifying threats and malicious activities. Moreover, understanding the foundational elements of AI’s role in threat detection is essential for leveraging its full potential. AI Artificial Intelliegnce Training Course in Lahore Pakistan
What Are the Potential Threats Posed by AI in Cybersecurity
It is important to understand that while cybersecurity and AI together can enhance security, AI can also be exploited by threat actors. Hackers can leverage AI in several ways to pose significant threats to cybersecurity. AI can automate and enhance social engineering attacks, psychologically tricking individuals into revealing sensitive information and compromising data integrity and confidentiality. Deepfake technology, powered by AI, can manipulate visual or audio content to impersonate individuals, leading to identity theft, misinformation, and other malicious activities. Hackers can also manipulate AI algorithms by feeding them deceptive information, resulting in incorrect outputs and potentially undermining the effectiveness of AI-based security systems. Furthermore, attackers can develop targeted malware that can evade AI-based detection systems, making it harder for traditional security measures to identify and mitigate these threats. Let’s explore some potential risks associated with AI from the perspective of cybersecurity professionals worldwide. As AI continues to enhance various aspects of cybersecurity, it also finds applications in more specific areas, such as ethical hacking. One notable example is ChatGPT, which has been adapted to assist ethical hackers in numerous ways, showing how versatile and adaptable AI can be in addressing modern cybersecurity challenges. Artificial Intelliegnce and Cyber Security Training Course in Lahore Pakistan
|
 |
Mr. Ammar Jaffar Chairman PISA Pakistan Information Security Association, FIA & Cyber Security Selected! Mr. Abbas Shahid Baqir (Director Student Shelter In Computers) Become PISA Pakistan Information Security Association (Board Member, Coordinator Punjab & Lahore Chapter) gave responsibilities to work on Schools, Colleges, Universities, Education Sector, Govt. Organization, Banks, Private Sector & Misc. Organization on Cyber Security Awareness, Certified Ethical Hacking CEH Awareness, Cyber Drills, COP Child Protection Law Projects , Digital Forensic , Computer Forenisc Investigation. As PISA Coordinator Punjab, has provided cyber expertise to state and local law enforcement on investigations of crimes, including homicides, stalking, missing children, cyber-bullying, and internal affairs. As Certified Cyber Security instructor, we developed a cyber-based curriculum and has trained hundreds of law enforcement and private professionals in evidence acquisition, security policy and implementation, breach response and mitigation, hacker methodology, and employee Internet safety. We Invited all Security Agencies, Organization, Companies, Colleges & Universities Students, Professors, Deans Organized Workshop / Seminars on Cyber Security, Ethical Hacker & Child Online Protection Programs and Invited us Student Shelter In Computers team we will work with them |

Importance of Ethical Hacking ?
In the dawn of international conflicts, terrorist organizations funding cybercriminals to breach security systems, either to compromise national security features or to extort huge amounts by injecting malware and denying access. Resulting in the steady rise of cybercrime. Organizations face the challenge of updating hack-preventing tactics, installing several technologies to protect the system before falling victim to the hacker.
New worms, malware, viruses, and ransomware are primary benefit are multiplying every day and is creating a need for ethical hacking services to safeguard the networks of businesses, government agencies or defense.


Designed &
Developed by Webmaster Abbas Shahid Baqir
Webmaster Feedback: [email protected]
All Rights
Reserved Copyright, 2010-2030 Student Shelter In Computers
®












.png)




